Dec 13, 2024
A One-Stop Look at the 2024 TON Ecosystem Technical Insights and Major Security Incidents
With the rapid development of blockchain technology, various ecosystems have emerged, one after another. Among them, the TON (The Open Network) ecosystem, created by Telegram, has gradually become a focal point in the industry due to its unique architecture and powerful functionalities. Another key factor lies in Telegram’s massive user base—over 700 million active users—providing a broad foundation for the promotion and application of TON.
In 2024, the TON ecosystem achieved significant progress in technological innovation, application expansion, and security protection. This article will present a comprehensive analysis of the fundamental architecture of the TON ecosystem, its flexible proof-of-stake mechanism, its extended use cases, and advantages, as well as the recent major security incidents and the responses taken. The aim is to offer readers a thorough view of the TON ecosystem.

Basic Introduction and Architecture
TON (The Open Network) is a blockchain and digital communication protocol created by Telegram that is designed to build a fast, secure, and scalable blockchain platform. It aims to provide users with decentralized applications and services by combining blockchain technology with Telegram’s communication features. TON is characterized by its high performance, robust security, and scalability. It supports developers in creating diverse, decentralized applications and offers distributed storage solutions. Compared to traditional blockchain platforms, TON boasts faster processing speeds and higher throughput and operates on a Proof-of-Stake (PoS) consensus mechanism.
Flexible and Sharded PoS Architecture
TON adopts a Proof of Stake (PoS) consensus mechanism and achieves high performance and multifunctionality through its Turing-complete smart contracts and asynchronous blockchain. The lightning-fast and low-cost transactions of TON are supported by the chain’s flexible and shardable architecture. This architecture allows for easy scalability without sacrificing performance. Dynamic sharding involves initially developed separate shards, each with its own purpose, which can run simultaneously and prevent large-scale congestion. TON’s block time is 5 seconds, and finality occurs in less than 6 seconds.
The existing infrastructure consists of two main components:
Masterchain: Manages all critical protocol data, including validator addresses and staked token amounts.
Workchains: Sub-chains connected to the Masterchain, containing all transaction information and various smart contracts. Each Workchain can operate under distinct rules.
This layered architecture not only enhances the network’s efficiency but also provides a solid foundation for future expansion.
Expanded Use Cases and Advantages
Under a robust technical framework, the TON ecosystem achieved remarkable advancements across multiple fronts in 2024. Operated by the core TON community, the TON Foundation functions as a decentralized autonomous organization (DAO) and provides comprehensive support for various projects within the ecosystem. This support includes developer assistance and liquidity incentive programs. Specifically, the TON community has excelled in the following areas:
Launch of TON Connect 2.0: Provides an intuitive way to connect wallets and applications, significantly improving user experience.
TON Verifier: A smart contract checker created by the Orbs team, enhancing contract reliability.
Blueprint Development Tools: Helps developers write, test, and deploy smart contracts.
Sandbox Developer Toolkit: Suitable for various use cases from enterprises to governments.
Support for Tact, Func, and Other New Languages: Promotes a more robust programming environment.
Developer Support: The TON Foundation collaborated with DoraHacks to launch a three-month online hackathon.
Internationalization of TON Hubs: Established international centers in multiple cities worldwide.
DeFi Liquidity Incentive Program: Provides funding for projects, promoting the sustainability of the TON DeFi sector.
These initiatives drive the ecosystem’s prosperity and create a more prosperous, more secure environment for developers and users.
Security Incidents in the TON Ecosystem
Although the TON ecosystem has made numerous advances in both technology and applications, security issues remain an essential aspect that cannot be ignored.
Recently, in the release notes of its latest version update, the official TON team formally thanked the TonBit security team under BitsLab for discovering a critical vulnerability in the TON virtual machine. If maliciously exploited, this vulnerability could lead to resource exhaustion of the virtual machine and system crashes, thereby affecting the stability of the entire TON network. Leveraging their profound technical expertise, the TonBit team quickly pinpointed the problem and proposed an effective solution, thereby constructing a more secure operating environment for the TON virtual machine and further enhancing the overall stability of the TON ecosystem.
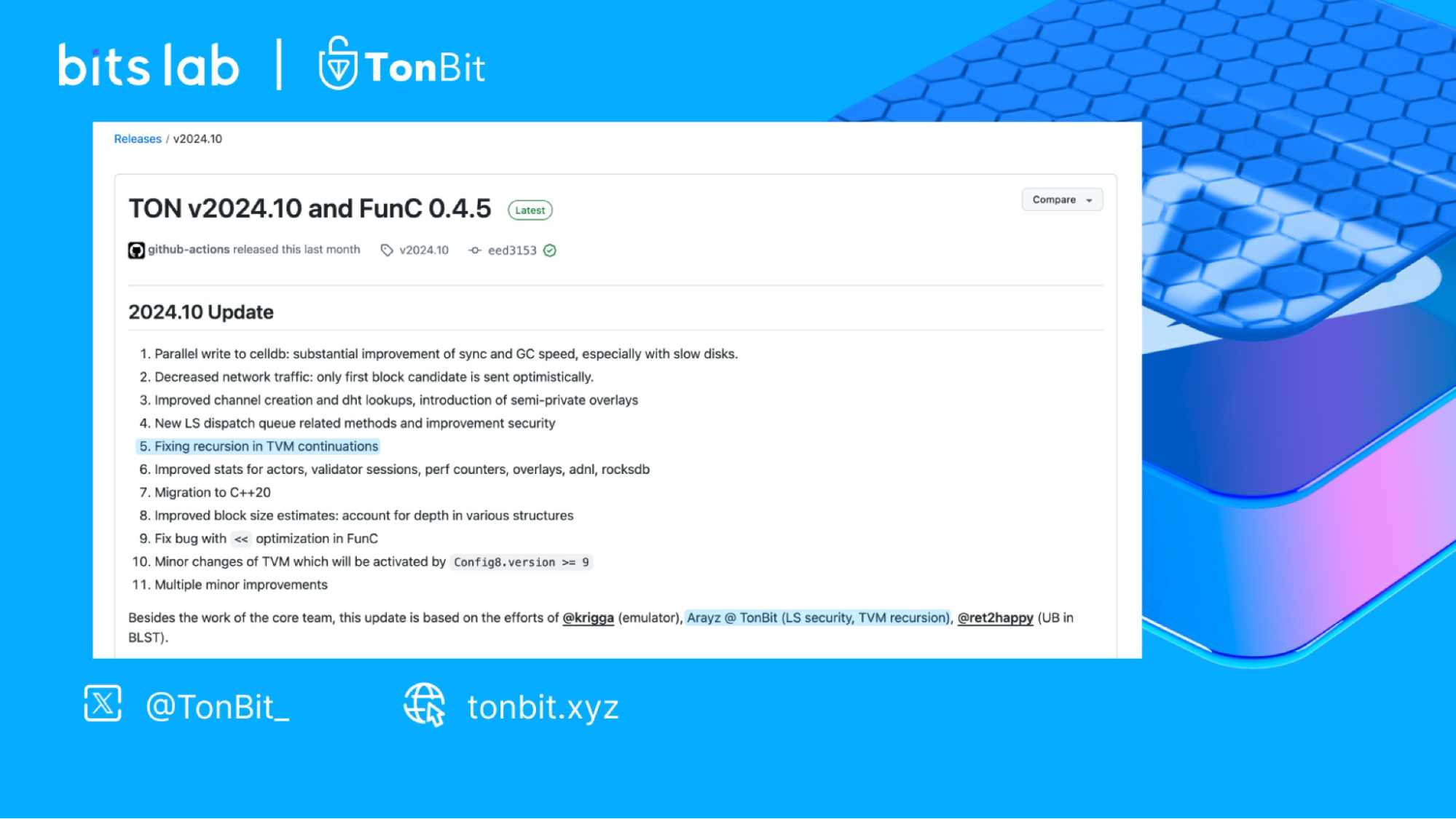
The root cause of this vulnerability lies in the risky nested operations design in the TON virtual machine when handling contract continuations. Malicious contracts could create deeply nested continuation structures that trigger a recursive evaluation process, thus depleting the host stack space of the virtual machine. This type of resource exhaustion attack could lead to abnormal crashes of the TON virtual machine. In simple terms, without spending even a single TON, one could cause all validators to go offline, directly affecting the availability of the system.
After in-depth analysis and collaboration with Ton Core, the TonBit team proposed an innovative solution. This solution adjusts the VM’s internal jump mechanism to replace recursive calls with iterative methods, effectively preventing such attacks. The solution has been applied in the latest version of TON, providing users with a more secure and stable operating experience.
In response to this major security incident, the TON team understands the importance of continuously strengthening security defenses. To ensure the long-term stability and security of the ecosystem, the team not only promptly fixed the vulnerability but also actively summarized their experiences and formulated more comprehensive security strategies. Based on this, we will explore how the TON ecosystem can further enhance security in the future, ensuring that as it rapidly evolves, it can effectively address potential security challenges.
Moreover, on May 22, 2024, after a staking event to celebrate the prosperity of the TON ecosystem, a certain protocol’s staking contract was attacked by hackers due to incorrect parameter configurations, resulting in the theft of a large number of tokens from the contract. After the incident, the project team immediately suspended the staking rewards redemption function and allocated a large amount of USDT to buy back the 307,264 lost tokens.
Following the attack, the project team quickly contacted TonBit for an audit. TonBit demonstrated professionalism by responding swiftly and mobilizing a team of security experts to conduct a comprehensive and meticulous security audit of the project’s core code. TonBit’s security experts discovered six low-risk issues and promptly engaged in detailed communication with the project team. Drawing on their rich experience and professional technical capabilities, TonBit provided specific solutions for the issues and assisted the team in quickly completing all the necessary fixes, ensuring the contract’s security and stability.
Additionally, on May 10, 2024, the TonBit team under BitsLab discovered that, while it is possible to add comments when processing “transfers” messages in TON, the UI design of some wallets when displaying these comments poses potential misleading risks. Hackers could exploit this design flaw by manipulating transfer message comment content, thereby showing users false information during transactions. This could lead to fraudulent activities, causing users to make erroneous operations and suffer financial losses.
To resolve this issue, TonBit recommended that wallet applications add conspicuous annotations when displaying such information, reminding users that this content may not be reliable. Furthermore, wallet development teams should improve their UI design to ensure the transparency and reliability of displayed transaction information. At the same time, users need to increase their discernment and remain vigilant against suspicious transaction information.
TonBit suggests that wallet development teams introduce a multi-layer verification mechanism when displaying transaction annotations. For example, verify the source of the annotation information to ensure its reliability. In addition, regular user education, such as issuing security reminders, can help users identify and guard against potential fraudulent activities. Combining technical measures with user education can effectively reduce such security incidents.
There are also incidents similar to BookPad’s use of a backdoored contract to swindle funds and then run off with the money, which should be highlighted for effective prevention. On April 15, 2024, BookPad released a closed-source smart contract containing a backdoor and began a presale activity. After receiving sufficient funds, they exploited the contract’s backdoor to withdraw the funds and then quickly absconded.
To prevent similar incidents from happening again, users should, before participating in any project’s investment activities, gather as much information as possible about the project team and choose those that are open-source and have undergone rigorous security audits.
In summary, although the TON ecosystem has made significant progress in technology and applications, security issues still need to be addressed. The TonBit team under BitsLab has effectively enhanced system security and stability by promptly discovering and helping to fix critical vulnerabilities, and they have demonstrated professional auditing and problem-solving capabilities in multiple security incidents. In the future, the TON ecosystem will continue to strengthen security measures and improve security strategies to ensure that, while evolving rapidly, it can effectively respond to various potential security challenges and protect the long-term security of users and the network.
Next, we will explore how the TON ecosystem, as it continues to expand and develop, can further enhance security to ensure robust system operation and user trust. To this end, the TonBit team, through a detailed analysis of the current security challenges faced by TON and advanced protection technologies that can be adopted, recommends implementing strict security audits to build an even more secure and reliable ecosystem. Through these measures, the stability of the TON network and user trust will be significantly strengthened, thereby promoting the sustainable and healthy development of the TON ecosystem.
Security Outlook for the TON Ecosystem
As the TON ecosystem rapidly expands decentralized applications (dApps) and infrastructure, its unique architecture and functionalities present some distinctive security challenges. The following are security recommendations and best practices for developers within the TON ecosystem:
Node Distribution and Protection: TON utilizes sharding and Distributed Hash Table (DHT) technology to enhance network scalability. However, uneven node distribution or insufficient protection could allow malicious nodes to dominate the network, conducting routing table pollution or network partition attacks. Developers should strengthen node verification mechanisms and enhance network defense capabilities by increasing node monitoring and implementing blacklist mechanisms.
Security of Smart Contracts: TON’s smart contract programming differs from other public chains, with more complex contract logic. Developers should strictly adhere to best practices for secure development, focusing on resource management and boundary checks in the code to avoid common contract vulnerabilities. Conducting code audits, regular reviews, and contract testing tools can improve code reliability.
Data Integrity and Tamper Prevention: TON’s distributed storage enhances data sharing and accessibility and introduces tampering risks. Developers can introduce multi-layered data encryption and authentication mechanisms and implement data consistency verification between nodes to ensure the integrity of data transmission.
Implementing these measures allows the TON ecosystem to maintain high security and stability while continuously expanding, providing more reliable services for users and developers.
Conclusion
In 2024, the TON ecosystem has made significant progress in technical architecture, application expansion, and security protection. Its flexible and shardable PoS architecture, high-performance transaction processing capabilities, and rich developer tools have laid a solid foundation for the prosperity of the ecosystem.
At the same time, facing security challenges, the TON official team has closely collaborated with security experts to promptly fix critical vulnerabilities, further enhancing the system’s stability and security. As the TON ecosystem continues to develop, continuously focusing on and improving security defenses will be crucial for its long-term sustainable growth. The ongoing advancements in the TON ecosystem provide new insights for developing blockchain technology and creating a safer and more efficient digital world for users and developers.
About TonBit
TonBit, as the core sub-brand of BitsLab, is a security expert and early builder within the TON ecosystem. As a Primary Security Assurance Provider for the TON blockchain, TonBit focuses on comprehensive security audits, including audits of Tact and FunC languages, ensuring that TON-based projects possess integrity and resilience.
To date, TonBit has successfully audited several well-known projects on TON, including Catizen, Algebra, and UTonic, and has discovered multiple critical vulnerabilities, showcasing our outstanding capabilities in the blockchain security field. Additionally, TonBit has successfully hosted the TON CTF competition, attracting numerous participants and garnering widespread attention, further solidifying its position as a security expert within the TON ecosystem. TonBit will continue safeguarding blockchain security in the future, driving the continuous development of technology and the ecosystem.
About BitsLab
BitsLab is an organization dedicated to the security of the Web3 ecosystem, aiming to become a respected security institution for the industry and users. It has three sub-brands: MoveBit, ScaleBit, and TonBit. BitsLab focuses on infrastructure development and security audits for multiple ecosystems, including Sui, Aptos, TON, BNB Chain, Starknet, and Solana, and is proficient in auditing various programming languages such as Circom, Halo2, Move, and Cairo.
As a leader in the blockchain security field, BitsLab provides security audit services for numerous projects, including Movement, Aptos, Tether, UniSat, and Nervos CKB. It has delivered over 400 security solutions, audited over 400,000 lines of code, protected assets worth $8 billion, and served over 2 million users. The team comprises top-tier vulnerability research experts who have discovered critical vulnerabilities in multiple renowned projects. BitsLab is committed to advancing Web3 security and fostering
emerging ecosystems’ healthy growth.
Official Website: https://bitslab.xyz/
BitsLab Twitter:https://x.com/0xbitslab
Official Telegram:https://t.me/BitsLabHQ
BitsLab’s Sub-Brand:
TonBit: https://www.tonbit.xyz/
MoveBit: https://www.movebit.xyz/
ScaleBit: https://www.scalebit.xyz/
Audit needs to contact Telegram:@starchou
Media Team: han@bitslab.xyz