May 20, 2025
Exclusive Interview with TonBit Under BitsLab| Continuously Safeguarding the TON Ecosystem with Innovation and Expertise
The thriving development of the TON ecosystem has always been built on a solid foundation of innovation, decentralization, and community collaboration. In this digital landscape, TonBit, under BitsLab, as an officially recognized Primary Security Assurance Provider (PSAP) for TON, has steadfastly upheld its mission as a guardian of TON network security.
To date, TonBit has completed security audits for over 30 key TON projects, successfully identifying and assisting in fixing multiple vulnerabilities on TON. At the same time, through initiatives such as the TON CTF competition and TON Global Hackerhouse events, TonBit continues to infuse security into the ecosystem and provide sustained momentum for innovation in TON projects.
As the TON ecosystem expands into multiple domains and dimensions, TonBit is leveraging its professional security expertise to build a more robust line of defense for the entire ecosystem. In this interview, we will delve into TonBit’s technical accomplishments and plans in depth.

Q1: Could you introduce TonBit and its role in the TON ecosystem?
TonBit: TonBit is the core sub-brand under BitsLab. As a trusted Primary Security Assurance Provider (SAP) and early builder in the TON ecosystem, we are committed to strengthening TON infrastructure security by delivering comprehensive security audits, vulnerability detection, and proactive penetration testing.
As an officially recognized SAP by the TON Foundation, we specialize in auditing smart contracts written in Tact and FunC, ensuring that projects built on TON maintain technical robustness and long-term resilience.
Q2: What services does TonBit provide for TON ecosystem projects?
TonBit: We primarily offer two core services:
Smart Contract Audits: In-depth code reviews for Tact/FunC contracts
Penetration Testing: Proactive security assessments for high-impact Web3 projects
To date, we have completed security audits for over 30 TON projects, including key projects such as Tonstakers, Torch Finance, Fiva Protocol, Duckchain, and Catizen.
Additionally, we have achieved significant results in vulnerability discovery, having identified and assisted in fixing three vulnerabilities on TON, including:
One critical vulnerability
One medium-risk vulnerability
One TON RUNVM vulnerability
Q3: What was the original purpose behind TonBit hosting the TON CTF competition?
TonBit: The TON CTF competition was designed to foster a security-first culture within the TON ecosystem. Its goals were to attract and challenge security experts and developers, with participants tackling challenges using FunC and Tact programming languages.
We believe TON CTF serves as a valuable and engaging way for TON developers to enhance their skills and explore the field of security, driving innovation, skill development, and deeper understanding of FunC and Tact within the TON ecosystem.
The event drew participation from over 20 global universities and security organizations, with more than 300 teams competing, significantly raising security awareness among participants in the TON ecosystem. More than just a competition, it served as an incubation platform for the next generation of TON security guardians.
Q4: How does the TON Global Hackerhouse event promote ecosystem development?
TonBit: In 2025, we co-hosted TON Global Hackerhouse with TON Official, TONX, TON Society, and TON Core, bringing together global developers to build the TON ecosystem jointly. The event not only attracted top-tier projects to participate and garnered millions of dollars in exposure but also drove innovative breakthroughs in the decentralized finance field, fully demonstrating TON’s real-world application potential as a scalable blockchain.
As the designated security guardian of the TON ecosystem, TonBit has always maintained high vigilance against various potential threats. In this in-depth interview, the TonBit security team provided a detailed analysis of three vulnerability discoveries, ranging from a “Critical”-level risk capable of paralyzing the network, to a “Medium-risk” vulnerability affecting system performance, and even complex attack vectors at the virtual machine level. Each case demonstrates TonBit’s exceptional technical capabilities and its “prevention-before-cure” security philosophy.
Q5: Regarding the critical TON Virtual Machine vulnerability discovered by TonBit in 2024, could you elaborate on its impact?
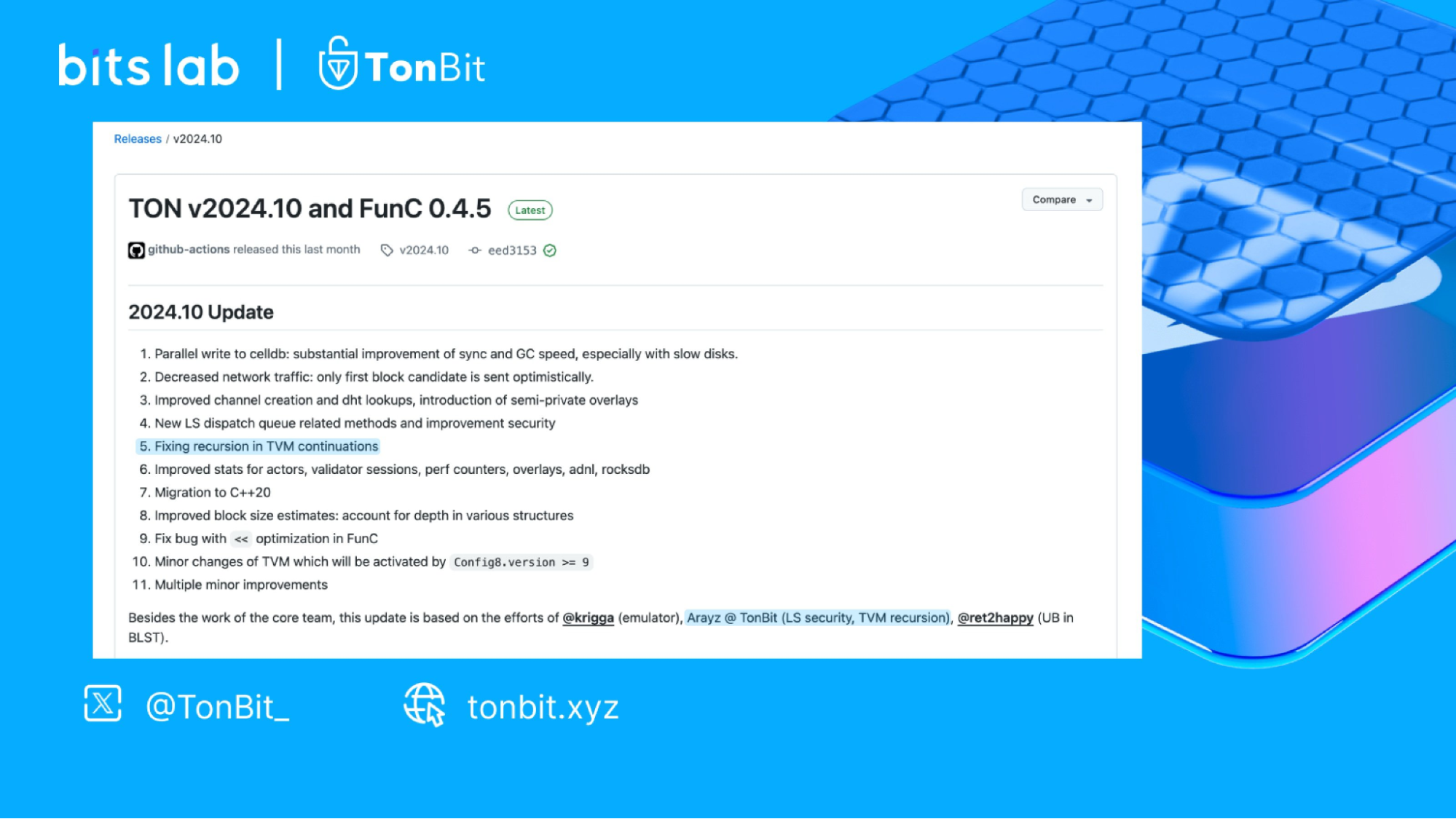
TonBit: In November 2024, the TON official team formally acknowledged the TonBit security team under BitsLab in their latest version update notes for discovering a critical vulnerability in the TON Virtual Machine. If maliciously exploited, this vulnerability could lead to virtual machine resource exhaustion, system crashes, and ultimately affect the stability of the entire TON network.
The root cause of this vulnerability lay in the risky design of nested operations when the TON Virtual Machine handled contract continuations. Malicious contracts could create deeply nested continuation structures, triggering recursive evaluation processes that would exhaust the virtual machine’s host stack space. This resource exhaustion attack could cause abnormal crashes of the TON Virtual Machine - simply put, without spending a single TON, it could bring down all Validators, directly impacting system availability.
Through in-depth analysis, the TonBit team collaborated with Ton Core to propose an innovative solution. This solution modifies the virtual machine’s internal jump mechanism by replacing recursive calls with iterative approaches, effectively preventing such attacks. The solution has been implemented in the latest version of TON, providing users with a more secure and stable operating experience.
Q6: How did TonBit address another vulnerability in TON light nodes?
TonBit: In November 2024, we also discovered a “Continuation Parameter Abuse Vulnerability” in TON light nodes. The core issue was that attackers could exploit deeply nested Continuation parameters to exhaust a node’s computational resources. In simple terms, this vulnerability allowed seemingly legitimate requests to keep nodes busy indefinitely. Imagine a car that appears normal but has a hidden flaw causing it to consume excessive fuel constantly—that’s essentially what this vulnerability did, silently consuming computing resources and affecting the network’s overall throughput.
Ultimately, by optimizing the parameter processing logic, we helped the TON team enhance the performance of light nodes, ensuring network efficiency and resilience against such attacks.
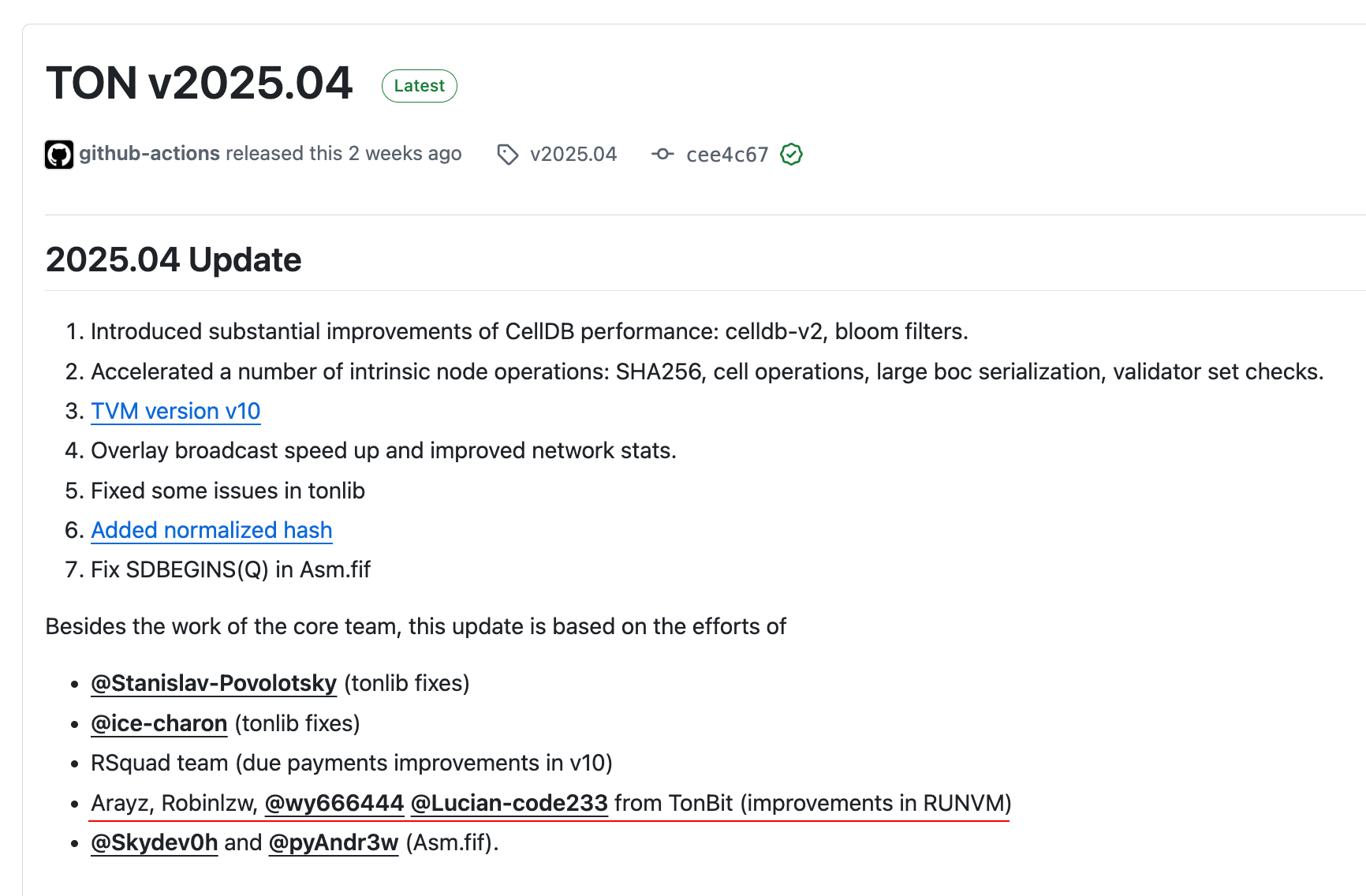
Q7: What was the impact of the TON RUNVM vulnerability discovered in 2025?
TonBit: This vulnerability involved non-atomic state migration in RUNVM instructions, where attackers could exploit the precise moment when a child virtual machine exhausted its gas to contaminate the parent VM’s libraries and induce subsequent call failures. This chain of exploitation would ultimately lead to abnormal behavior in any contracts that depended on library integrity.
Upon discovery, we promptly submitted the complete technical details along with comprehensive mitigation solutions to the TON Foundation, while actively assisting them through the entire remediation process. We strongly advised all developers in the ecosystem to take three crucial actions: immediately update all dependency libraries once official patches became available, implement more rigorous library integrity verification protocols, and significantly enhance gas management logic within their self-developed contracts. These collective measures have created an effective defense against potential malicious exploitation of similar vulnerabilities in the future.
Q8: What unique advantages does TonBit have compared to other blockchain security companies?
TonBit: Our core competitiveness is reflected in three key dimensions:
- TON-Specific Technical Expertise: We are not only proficient in Tact and FunC programming languages but also possess specialized penetration testing and vulnerability discovery capabilities.
- Deep Ecosystem Integration: As an officially recognized SAP (Security Assurance Provider), we are deeply committed to safeguarding the TON ecosystem, having already audited over 30 critical projects within the TON network.
- Community Co-Building Capabilities: Through initiatives such as CTF competitions and TON Global Hackerhouse events, we actively enhance community engagement, elevate security awareness, and foster ecosystem development.
We go beyond mere code auditing – we are dedicated to building an impenetrable ecosystem.
Q9: What are TonBit’s key initiatives for 2025-2026?
TonBit: We will focus on advancing three strategic priorities:
Sustained TON Ecosystem Protection:
We will continue providing reliable security audits for TON ecosystem projects, develop automated scanning tools for Tact/FunC smart contracts, and enhance penetration testing and vulnerability discovery efforts to build a comprehensive security framework for the entire ecosystem.Industry-Academia-Research Collaboration:
By establishing joint laboratories with leading academic institutions, we will conduct specialized research on the security of the TON ecosystem.Developer Empowerment Program:
We will elevate developer security awareness through targeted training courses and hands-on exercises, because a secure TON ecosystem begins with education as its foundation.
Closing: TonBit remains dedicated to its role as TON’s security cornerstone. By merging cutting-edge research with community-driven initiatives, they’re shaping a future where innovation thrives on a foundation of trust. To learn more, visit TonBit’s GitHub or follow our updates on X (Twitter).